The Developer's Guide to SaaS Compliance
Aman Kandola
June 09, 2022

As SaaS applications usually collect and process sensitive user information, keeping this information secure is key to building user trust and ensuring long-term business success. One of the ways for SaaS providers to communicate how exactly their users’ data is kept safe is through compliance with security and privacy standards. Compliance certifications are an effective way to communicate that you’re meeting industry standards and handling user data in alignment with customer expectations, all through a standardized report that customers know how to read.
This post is the second in a series about what developers need to keep in mind when sorting out security and compliance for their application. The first article in this series covered how to build security for user communications and in this one, we will review what kinds of compliance certifications and regulations exist for SaaS applications, what these certifications mean for developers, and how to begin the certification process for compliance standards.
Why are compliance standards and certifications useful?
Compliance with a standard means that your SaaS application adheres to certain security criteria as recognized and verified by a reputable outside organization. These standards might be based on legal regulations or industry best practices. Certified compliance in the data management area, for example, indicates that you are following best practices when processing user data, and customers are more likely to trust you with their data because of it.
For many SaaS companies, compliance certifications are an effective way to communicate their security stance and trustworthiness to prospective customers. A prospect doesn't need to perform their own security audit on your infrastructure if they can see that a set of standardized checks have already been run successfully and reported on by a qualified independent party. You can produce the report once and then share it with any number of prospects over time with no additional time investment.
Besides voluntary compliance, there are also legal requirements to follow if your services are available in certain regions or collect particular types of data—for example, medical records. Not complying with legal regulations or contractual requirements can incur financial penalties and other potential consequences for your company.
Common certifications for SaaS applications
In this section, we will cover a few of the existing compliance standards relevant for SaaS companies. The certification process is typically done over a period of time and involves a significant investment of time and resources from the company’s side.
SOC 2
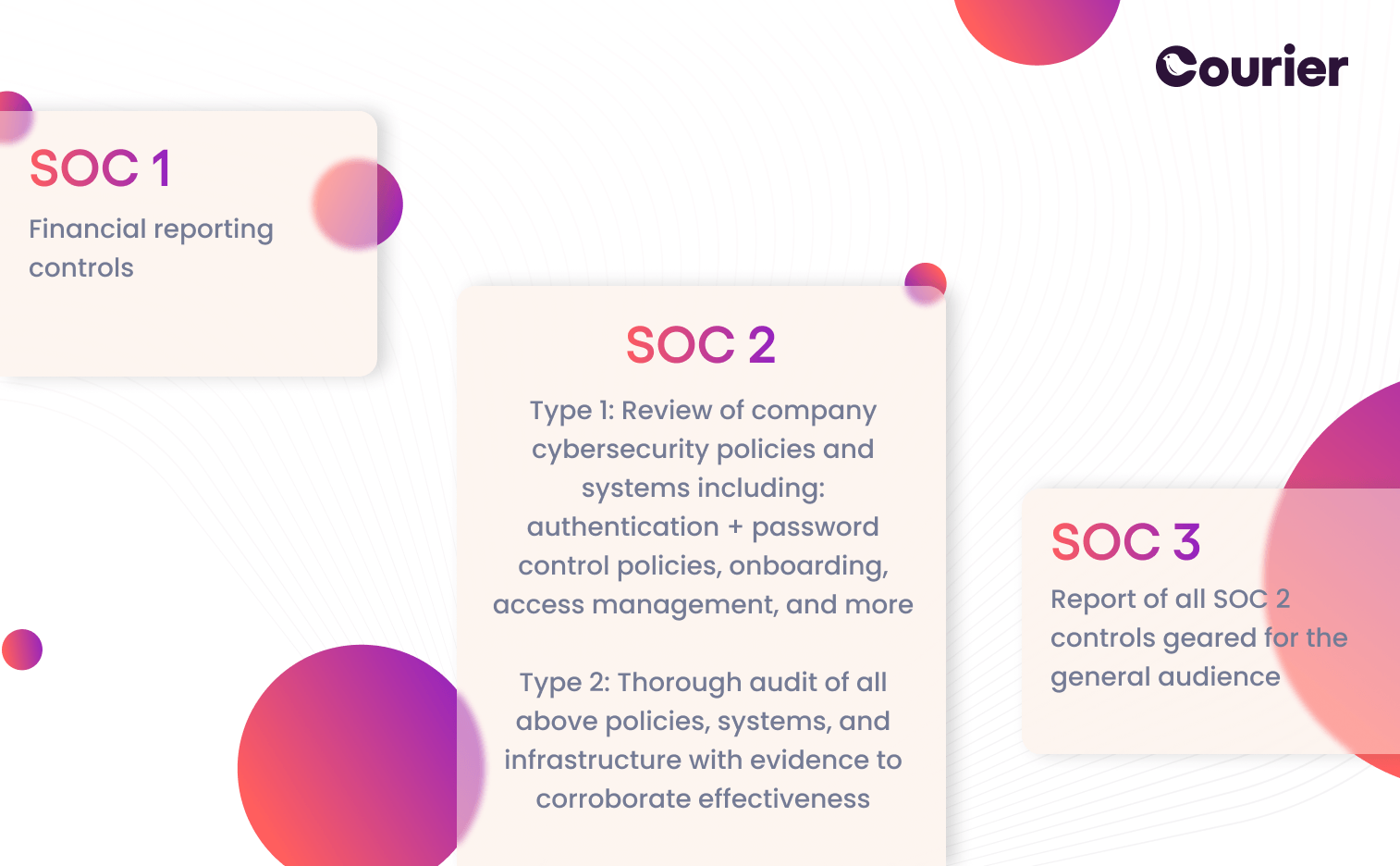
SOC (Service Organization Control) audits were developed by the American Institute of Certified Public Accountants (AICPA) as a way to examine an organization's risk management. SOC1 audits are primarily for financial reporting controls, while SOC 2—most relevant to SaaS applications—audits an organization’s risk in multiple areas, including organizational governance, operations, cybersecurity, and process consistency. The audit is performed by an external auditor who is required to be a Certified Public Accountant (CPA).
The output of a SOC certification is a report by the SOC auditor that describes the audited company’s performance on the SOC criteria. At the SOC 2 level there are two types of reports: Type 1 is a review of company policies, procedures and the design of internal controls, whereas Type 2 requires the company to demonstrate that their policies, procedures and internal controls operate effectively over a specified period of time. As of 2022, Courier completed their SOC 2 Type 2, and you can read more about how the certification works and Courier’s experience with it in this blog post.
For SaaS companies, a successful SOC report offers evidence that the application is actually adhering to the security measures that it purports to follow, and that these measures are efficient in protecting customers’ sensitive information. Security-conscious customers are more likely to purchase software from SOC-compliant vendors.
ISO/IEC 27001
ISO/IEC 27001 is an international data management standard that organizes security controls by establishing an information security management system (ISMS). SaaS providers must perform their own audits to measure their compliance with the ISO standard, and only then can they request an external audit. External audits are thorough and include documentation review, supporting evidence of actual processes, and reviews of management policies. The certification has to be renewed every three years.
The benefits of the ISO/IEC 27001 certification include a robust security control system, and again, improved business opportunities and reputation. Additionally, as ISO/IEC 27001 is a leading international standard, it follows similar requirements and overlaps with the information security requirements of the SOC 2 audits.
ISO also has other standards, such as ISO 27018 and 27701, that are relevant to privacy and overlap with privacy laws and regulations such as GDPR that we cover below.
FedRAMP
The Federal Risk and Authorization Management Program (FedRAMP) is a compliance standard that verifies whether your application infrastructure adheres to highly sensitive data management that meets the requirements of the U.S. federal government.
The U.S. government deals with a massive amount of delicate data; any security breaches can have far-reaching consequences, including financial losses or threats to national security. Within FedRAMP, there are different levels of authorization depending on whether the data managed is classified or unclassified and the impact level in case of a breach. FedRAMP is based on the National Institute of Standards and Technology (NIST) 800-53 comprehensive security controls, so a FedRAMP-compliant application will need to follow that paradigm if you’re aiming for federal contracts.
The benefits of complying with the FedRAMP standards for SaaS, Infrastructure-as-a-Service (IaaS), or Platform-as-a-Service (PaaS) organizations can be enormously lucrative, especially if they are the only company among competitors with such a certification, as this authorization expands business opportunities for large contracts with U.S. federal agencies.
Compliance with legal requirements
Besides voluntary compliance certifications, there are legal requirements that any SaaS provider must follow if they choose to conduct business in particular regions or to process specific private information.
General Data Protection Regulation
The EU General Data Protection Regulation (GDPR) is a strict data privacy and security law in Europe. It was enacted in 2018 and carries severe financial penalties for non-compliance. This regulation applies to any organization worldwide if it handles any personal data belonging to EU residents. Depending on your SaaS business model, you might or might not fall under GDPR requirements.
GDPR attempts to minimize the types and amount of user data collected by websites and applications. It also stipulates security control measures such as two-factor authentication (2FA) and access control for any accounts that store sensitive information, end-to-end encryption, training staff in data protection awareness, and a data privacy policy. In the event of a security breach, an organization is given 72 hours to disclose the breach or face severe penalties. Facebook, Google, and Amazon have already, since 2018, been fined huge sums for violating the GDPR’s privacy and security legal requirements. The penalties for violating the GDPR are high, to ensure that tech companies make changes instead of just accepting the penalty as the cost of doing business.
Legal requirements by U.S. states
States in the U.S. have begun following GDPR’s lead by instituting their own legal requirements for collecting and storing personal information. In January 2020, California enacted the California Consumer Privacy Act (CCPA), which follows similar requirements to GDPR but applies to California residents. Coming in second, in 2021 the state of Virginia passed the Virginia Consumer Data Protection Act (CDPA), applicable to any organization conducting business in Virginia or targeted toward Virginia residents.
Health Insurance Portability and Accountability Act
The Health Insurance Portability and Accountability Act (HIPAA) of 1996 is a U.S. federal law that protects patients from disclosure of sensitive health information without their consent. This law only applies to identifiable health information. If a SaaS provider in any way deals with data that falls under “protected health information,” the provider is legally required to comply with all HIPAA measures.
Under HIPAA, SaaS providers that have legal contracts with U.S. healthcare providers or managers need to have signed a Business Associate Agreement, which regulates responsibilities of parties and outlines specific steps to follow in case a breach occurs. HIPAA compliance is a requirement to be able to work with medical providers and lack of compliance will make pursuing business opportunities in the healthcare space much more difficult if not impossible.
What does compliance mean for a developer?
The important takeaway from any of these compliance standards is that good security controls, data privacy, and data management should be foundational components of a SaaS application from the beginning.
Certifications like SOC 2 focus on the consistency of internal processes, including the software design and development process. Ensuring that you have documented processes for planning, design, development, testing, and deployment of software and are following them consistently will make getting certified much easier. For the SOC 2 Type 2 report, your organization will also need to produce evidence that the processes are being followed, so automations and audit logs for various process steps will be essential.
Informative guides can explain how to build an application with a strong and secure foundation, such as the AWS Well-Architected Framework guide, especially if you’re using AWS as part of your infrastructure. We also recommend the Center for Internet Security’s (CIS) Controls and Benchmarks that establish best practices in contemporary cybersecurity.
What should you do if you want to get certified?
We asked Nick Norton from Geels Norton, a compliance audit and advisory firm that specializes in compliance for high-growth SaaS companies, for a few tips for SaaS companies looking to pursue compliance certifications. Here are his top recommendations.
1. Set up an internal team and define responsibilities
Most certifications require operational and technical work on the company side, and you will need to make sure that you have resources available to make that work happen within the certification timeframe. Nick strongly recommends having at least one C-suite sponsor as part of the compliance team to make sure necessary work items get prioritized in time.
The internal team should include both engineering and business stakeholders. Most SaaS companies don’t realize that around half of the compliance work will fall on the business operations side rather than pure software development and technical security.
2. Use automation tools
Even if your organization has the practices down, you will still need to spend time maintaining and collecting evidence of compliance. Therefore, it’s beneficial to invest in automated software tools like Vanta or Drata that can speed up the evidence collection process. These tools help manage and record evidence of compliance practices via continuous monitoring of the application’s infrastructure and business processes. When using software to continuously monitor internal control activities and collect evidence, it’s important that companies fully understand the capabilities and limitations of the software — there will always be important human elements of compliance initiatives.
3. Speak to an outside expert
A consultant with relevant experience will be able to save you time and resources by walking your company through the process ahead of time. They will identify appropriate control activities that fit your company’s risk profile and align with the relevant compliance requirements. For best results, make sure that the consultant has worked with companies similar to yours in the past.
The road to compliance
Compliance can be a costly process, but it can also open up lucrative business opportunities and new markets for expansion. If, as a SaaS provider, your services need to serve audiences with stringent data protection needs, then following compliance standards will also save your organization’s reputation and improve your competitive standing.
At the root, compliance is a form of risk management for any SaaS provider. There’s no way of keeping your application 100% foolproof against security breaches. Nonetheless, the standards outlined in this article will help you minimize the risk to your users—and therefore to your business.
Similar resources

Expo Push Notifications: The Complete Implementation Guide (SDK 52+)
Expo push notifications are alerts sent from a server to a user's phone, even when the app isn't open. To set them up, install the expo-notifications library, ask the user for permission, and get a unique push token for their device. Your server sends a message to Expo's push service with that token, and Expo delivers it through Apple or Google. Push notifications only work on real phones, not simulators. Local notifications are different — they're scheduled by the app itself for things like reminders. You can also route Expo push through services like Courier to add email, SMS, and Slack fallbacks.
By Kyle Seyler
February 24, 2026

Best Email API Providers for Developers in 2026: SendGrid vs Postmark vs Mailgun vs SES vs Resend
Your email provider sticks with you longer than most technical decisions. Courier handles notification infrastructure for thousands of teams, so we went deep on the six email providers that show up most: SendGrid, Postmark, Mailgun, Amazon SES, Resend, and SMTP. This guide covers real API primitives, actual code from each provider's docs, Courier integration examples with provider overrides, and an honest read on where each developer experience holds up and where it breaks down. We also asked Claude to review every API and tell us which one it would wire up first. The answer surprised us.
By Kyle Seyler
February 23, 2026
The Courier MCP Server Is Open Source. Here's How It Actually Works.
Courier's MCP server is open source at github.com/trycourier/courier-mcp. It connects AI coding tools like Cursor and Claude Code to your Courier account so they can send messages, manage users, and install SDKs without hallucinating API details. This post walks through the actual codebase: how 16 tool classes are registered (and how a config allowlist gates most of them), why we pull installation guides from GitHub at runtime instead of bundling them, how the DocsTools class generates live JWTs alongside setup instructions, and what the SdkContextTools class does in the repo to prevent v7/v8 SDK conflicts (even though it isn't wired into the server yet).
By Mike Miller
February 06, 2026
© 2026 Courier. All rights reserved.